Cyber Insurance Decoded: Understanding Your Coverage Needs
Cyberattacks are a serious threat, and cyber insurance helps mitigate the financial fallout. This listicle explains what cyber insurance covers, empowering you to choose the right policy. From data breaches and ransomware to regulatory fines and cybercrime, we'll cover seven key areas of protection. Understanding these components is crucial for individuals, families, and businesses alike – whether you're a homeowner, manage a business, or operate a fleet. Learn how cyber insurance safeguards your assets and what to consider for comprehensive coverage.
1. Data Breach Response and Notification Coverage
When considering "what does cyber insurance cover," data breach response and notification coverage stands as a cornerstone of any robust policy. This fundamental coverage addresses the immediate costs and legal obligations that arise in the chaotic aftermath of a cyberattack or data breach incident. In today's interconnected world, where sensitive data is constantly under threat, this type of coverage is not just beneficial, it's essential for businesses of all sizes, from small startups to multinational corporations, and even individuals handling significant amounts of personal data. This protection can be the difference between a manageable setback and a catastrophic financial and reputational crisis.
Data breach response and notification coverage encompasses a wide array of expenses and services designed to mitigate the damage and ensure compliance following a breach. This includes the costs associated with investigating the nature and extent of the breach, which often involves hiring specialized forensic investigators to identify vulnerabilities and determine the root cause of the incident. It also covers the legally mandated notification process, ensuring affected individuals are informed promptly and according to regulatory requirements. Furthermore, this coverage often extends to providing credit monitoring services to those whose data may have been compromised, helping to protect them from identity theft and other financial repercussions.
Beyond the immediate technical and legal requirements, this type of coverage also addresses the critical aspect of reputation management. A data breach can severely damage a company's image and erode customer trust. Cyber insurance policies typically include public relations and crisis communication support to help navigate the difficult process of communicating with stakeholders and minimizing reputational damage. This can involve crafting press releases, managing social media communications, and engaging with affected parties in a transparent and reassuring manner. Additionally, some policies offer protection against regulatory fines and penalties that may be imposed following a breach, further mitigating the financial impact. Finally, 24/7 incident response hotline access ensures swift action and expert guidance can be obtained immediately following a suspected breach.
The benefits of data breach response and notification coverage are numerous. It provides comprehensive support during critical breach incidents, helping businesses navigate the complex legal and technical landscape. It helps ensure regulatory compliance, minimizing the risk of hefty fines and penalties. Professional PR support reduces reputational damage and helps maintain customer trust. And perhaps most importantly, it provides access to specialized breach response teams who can quickly contain the incident and mitigate its impact.
However, this coverage is not without its limitations. Coverage limits may not fully cover the costs associated with massive breaches, especially for larger organizations. Prompt notification to the insurer is crucial for activating coverage, and delays can jeopardize the claim. Some policies may have waiting periods before coverage takes effect, leaving businesses vulnerable during the initial period after policy inception. Finally, pre-existing or known vulnerabilities are typically excluded from coverage, emphasizing the importance of proactive cybersecurity measures.
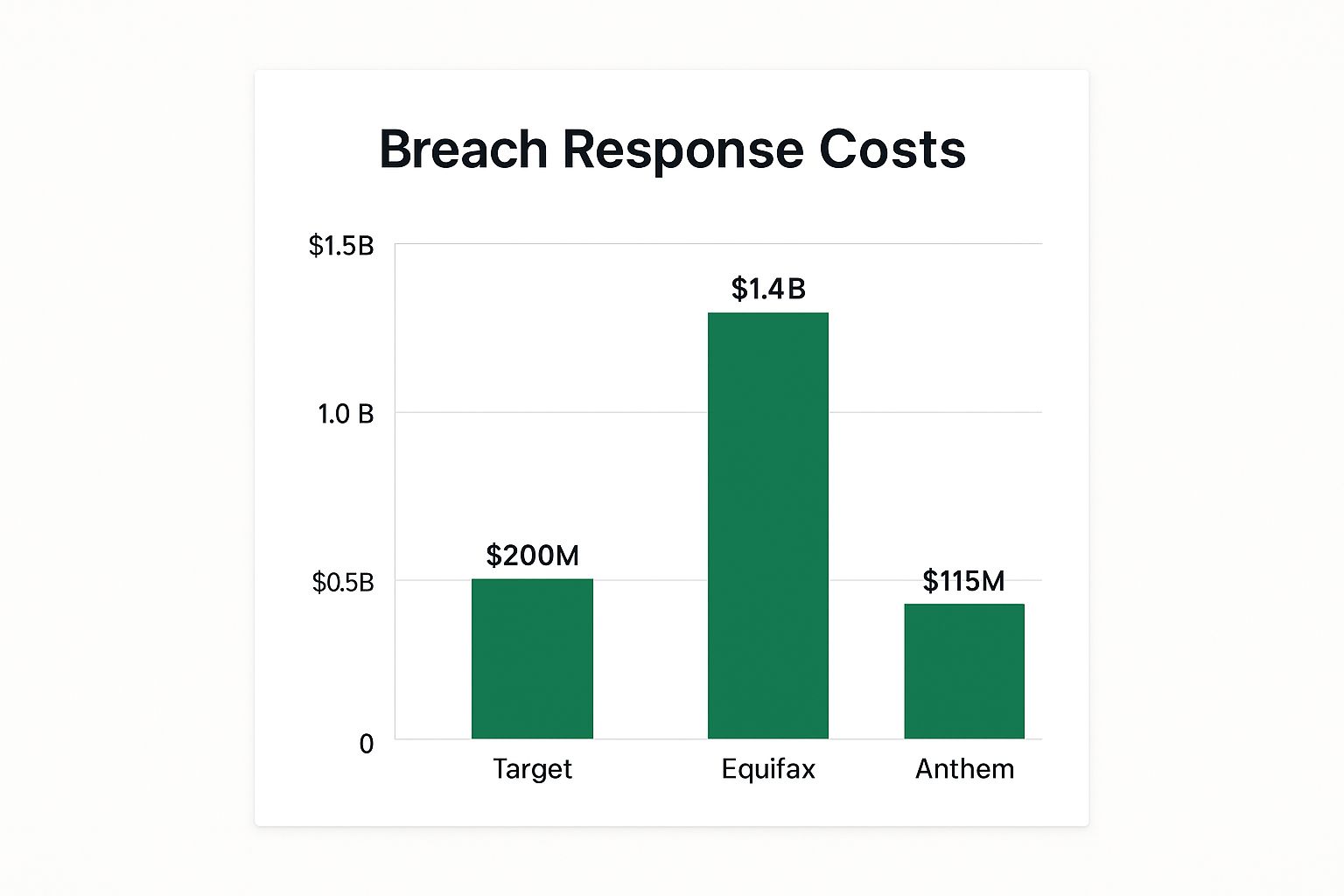
Several high-profile data breaches highlight the significant financial consequences of these incidents and the value of data breach response and notification coverage. Target's 2013 breach cost over $200 million in response efforts, encompassing legal fees, credit monitoring services, and public relations campaigns. Equifax spent approximately $1.4 billion on breach-related costs, a staggering figure that underscores the potential financial devastation of a large-scale breach. Anthem's 2015 breach resulted in $115 million in settlement costs, demonstrating the significant legal and financial ramifications of failing to adequately protect sensitive data.
The following infographic visualizes the data breach response costs for these three companies: Target, Equifax, and Anthem.
As the bar chart clearly illustrates, the costs associated with data breaches can vary dramatically depending on the scale and severity of the incident, with Equifax's costs dwarfing those of Target and Anthem.
To ensure you're adequately prepared, establish clear incident response procedures before a breach occurs. Maintain an updated inventory of sensitive data to understand your potential exposure. Review notification requirements for all jurisdictions where you operate to ensure compliance. And finally, consider higher coverage limits if your business handles large volumes of personal data. Learn more about Data Breach Response and Notification Coverage
2. Business Interruption and System Downtime Coverage
When considering what cyber insurance covers, business interruption and system downtime coverage stands out as a critical component for any business relying on digital systems. This type of coverage is designed to compensate businesses for the financial fallout that occurs when a cyber incident, like a ransomware attack or a system outage, disrupts their normal operations. It's not just about the immediate costs of dealing with the incident itself; it's about mitigating the ripple effect that downtime can have on a company's bottom line. This protection addresses the often substantial revenue losses incurred during these periods, along with the additional expenses required to get back up and running.
Imagine a scenario where a ransomware attack cripples your company's network. Orders can't be processed, customer service lines are down, and your website is inaccessible. Every minute of downtime translates directly into lost revenue. This is where business interruption coverage steps in. It aims to replace the income you would have earned had the cyber incident not occurred. But it goes beyond simply covering lost revenue. It also addresses the extra expenses you might incur as a result of the disruption. This could include the cost of setting up temporary operations, hiring external IT specialists, or even renting alternative office space.
This component of cyber insurance also recognizes the interconnectedness of businesses. Dependent business interruption protection extends coverage to losses suffered due to disruptions experienced by a key supplier or customer. Imagine your primary supplier is hit with a cyberattack, halting their production and, consequently, your supply chain. This coverage would help mitigate the financial impact of this indirect disruption. Furthermore, system restoration cost coverage helps with the often significant expenses associated with rebuilding compromised systems and recovering lost data. And, importantly, some policies even provide employee wage continuation during outages, allowing you to retain your workforce even when operations are temporarily suspended. Retaining customers during these trying times is also crucial, and some policies offer customer retention expense reimbursement to help cover the costs of communicating with customers, offering discounts, or other measures to maintain their loyalty.
The benefits of business interruption and system downtime coverage are clear: maintaining cash flow during cyber incidents, covering both direct and indirect business losses, helping preserve customer relationships, and supporting business continuity efforts. However, there are some important considerations. This type of coverage typically requires documented proof of actual financial losses, which necessitates meticulous record-keeping. There may also be waiting periods before coverage begins, similar to a deductible in terms of time, and the calculations for determining losses can be complex. It's also essential to note that losses from system upgrades or improvements are generally excluded, as these are considered capital expenditures rather than direct results of the cyber incident.
Real-world examples highlight the devastating financial consequences of cyberattacks and underscore the importance of this coverage. Maersk, the global shipping giant, lost an estimated $300 million due to the NotPetya ransomware attack, which crippled its operations worldwide. Similarly, FedEx subsidiary TNT Express suffered a $400 million loss from the same attack. The Colonial Pipeline shutdown, caused by a ransomware attack, resulted in an estimated $11.6 million per day in lost revenue. These examples clearly illustrate the potential financial devastation that cyber incidents can inflict on businesses of all sizes.
To ensure you're adequately protected, maintain detailed financial records to substantiate any loss claims. Develop and regularly test robust business continuity and disaster recovery plans to minimize downtime. When selecting a policy, consider shorter waiting periods if your operations are particularly time-sensitive. And finally, meticulously document all extra expenses incurred during the incident response process. Learn more about Business Interruption and System Downtime Coverage. Understanding what cyber insurance covers, particularly the crucial role of business interruption and system downtime coverage, is essential for navigating today's increasingly complex digital landscape and ensuring the long-term resilience of your business.
3. Ransomware and Cyber Extortion Coverage
Ransomware and cyber extortion are two of the most significant cyber threats facing individuals and businesses today. When considering what cyber insurance covers, this specialized coverage is crucial. Ransomware attacks involve malicious software that encrypts a victim's data, making it inaccessible until a ransom is paid. Cyber extortion, a broader term, encompasses various threats where attackers demand payment to prevent the release of sensitive data, disruption of services, or other harmful actions. This coverage addresses these threats by providing financial and expert support to victims. It helps individuals and organizations navigate the complex process of responding to these attacks, minimizing financial losses and reputational damage. This type of coverage is becoming increasingly important as cybercriminals become more sophisticated and the frequency of attacks rises.
This coverage typically includes several key features designed to mitigate the impact of ransomware and cyber extortion attacks. These features often encompass ransom payment coverage (with insurer approval), professional negotiation services with experienced negotiators, facilitation of cryptocurrency transactions (often the preferred payment method for attackers), and coverage for data recovery and system restoration costs. It can also include legal consultation for payment decisions, helping victims understand the legal and regulatory landscape surrounding ransom payments. Furthermore, enhanced monitoring services post-incident can help prevent future attacks. Understanding what cyber insurance covers in this context is vital for mitigating the risks associated with these increasingly common threats.
There are several advantages to having ransomware and cyber extortion coverage as part of your cyber insurance policy. Access to experienced ransomware negotiators is invaluable. These professionals understand the tactics employed by attackers and can effectively negotiate for a lower ransom or even secure the release of data without payment. This expertise also reduces the time to resolution, minimizing downtime and disruption. Professional guidance on complex payment decisions is another significant benefit, helping victims navigate the legal and ethical considerations involved. The comprehensive support beyond just payment coverage ensures that victims receive the assistance needed to fully recover from an attack. For everyone from homeowners to large companies, knowing what cyber insurance covers in this area can make a significant difference in their ability to recover from an attack.
However, there are also potential downsides to consider. One key concern is the ethical dilemma of funding criminal activities. Paying ransoms can incentivize further attacks and contribute to the growth of the cybercrime ecosystem. There is also no guarantee of data recovery even after payment. Attackers may not honor their agreements, or the data may be irreparably damaged. Regulatory restrictions on payments are another potential hurdle. Some jurisdictions prohibit or discourage ransom payments, and companies must be aware of these regulations. Finally, publicizing ransom payments can make a company a target for future attacks, as it signals a willingness to pay.
Several high-profile ransomware attacks highlight the importance of this coverage. The Colonial Pipeline paid $4.4 million to the DarkSide ransomware group, disrupting fuel supplies across the southeastern United States. JBS Foods paid $11 million to resolve the REvil ransomware attack, impacting meat production globally. CNA Financial reportedly paid $40 million following the Phoenix Locker attack. These examples demonstrate the significant financial consequences of ransomware attacks and the potential benefits of having appropriate insurance coverage.
To minimize reliance on ransom payments, implement robust backup systems and establish clear decision-making protocols for ransom situations. Consider the legal and regulatory implications before making payments, and maintain offline backups that cannot be encrypted by attackers. These proactive measures can significantly reduce the impact of ransomware attacks and the need to pay a ransom. When considering what cyber insurance covers, ransomware and extortion coverage stands out as a critical component in today's threat landscape. From homeowners concerned about personal data to large corporations protecting sensitive information, understanding the nuances of this coverage is crucial.
4. Third-Party Liability and Privacy Claims Coverage
When considering what cyber insurance covers, third-party liability and privacy claims coverage is a crucial component, especially in today's interconnected digital landscape. This coverage protects your business from the financial fallout of lawsuits and claims filed by customers, partners, or other third parties impacted by a cyber incident originating from your systems. It essentially acts as a shield against the legal and financial repercussions of data breaches, privacy violations, and other security failures that harm external parties. This is particularly important given the increasing frequency and severity of cyberattacks and the growing emphasis on data privacy regulations.
This type of coverage addresses a wide range of expenses associated with cyber-related litigation. It covers legal defense costs, including attorney fees, expert witness fees, and court costs. Furthermore, it provides protection for settlements and judgments awarded against your business, preventing a single cyber incident from crippling your finances. Specifically, this coverage encompasses:
- Legal defense cost coverage: Cybersecurity lawsuits can be incredibly expensive to defend, even if the claims are ultimately unfounded. This coverage ensures you have the resources to mount a robust legal defense.
- Settlement and judgment payment protection: If a lawsuit results in a settlement or judgment against you, this coverage will help pay the associated costs, up to the policy limits.
- Privacy violation claim coverage: This addresses claims arising from unauthorized access, use, or disclosure of personal information.
- Regulatory investigation defense: Data breaches often trigger investigations by regulatory bodies. This coverage helps cover the legal costs associated with responding to and defending against these investigations.
- Class action lawsuit protection: Data breaches impacting a large number of individuals can lead to costly class-action lawsuits. This coverage helps mitigate the financial impact of such suits.
- Intellectual property infringement coverage: In some cases, a cyberattack can lead to the theft or misuse of intellectual property. This coverage can help protect your business from the resulting financial losses.
The benefits of third-party liability and privacy claims coverage are substantial. It provides comprehensive legal protection against a wide array of cyber-related lawsuits, safeguarding your business from potentially devastating financial consequences. It covers both individual and class-action claims, offering broad protection in various scenarios. The inclusion of regulatory defense coverage is particularly valuable, given the increasingly stringent regulatory environment surrounding data privacy. Moreover, many policies provide access to specialized cyber law attorneys who possess the expertise to navigate the complexities of cyber-related litigation.
However, like any insurance policy, there are potential drawbacks to consider. High deductibles may apply to discourage frivolous claims, meaning you’ll have to bear a significant portion of the initial costs. Coverage exclusions for intentional acts are common, so negligence or malicious actions by your employees might not be covered. Limits may be insufficient for large class-action lawsuits, especially if a significant number of individuals are impacted by a data breach. Finally, prior acts coverage, which covers incidents that occurred before the policy inception date, may be limited or excluded altogether.
Several high-profile cases highlight the importance of this type of coverage. Equifax faced over 240 class-action lawsuits after their 2017 breach, demonstrating the potential for massive legal exposure following a significant cyber incident. Yahoo paid $117.5 million to settle data breach class actions, while Capital One settled for $190 million following their 2019 data breach. These examples underscore the significant financial implications of cyberattacks and the critical role of cyber insurance in mitigating these risks.
To minimize your risk and maximize your protection, regularly review your privacy policies and security practices. Maintain comprehensive documentation of your security measures to demonstrate your commitment to data protection. Consider higher liability limits for businesses with extensive customer data, as the potential financial impact of a breach is directly correlated to the amount of data compromised. Finally, implement strong vendor management and due diligence processes to ensure that your partners and suppliers adhere to robust security standards.
When deciding if this coverage is right for you, consider your business's specific needs and risk profile. If you handle sensitive customer data, operate in a highly regulated industry, or are concerned about the potential financial impact of a data breach, then third-party liability and privacy claims coverage is likely essential. This type of coverage is particularly relevant for homeowners with smart home technology, high-net-worth families concerned about reputation damage, businesses of all sizes, professionals offering online services, and anyone handling sensitive information electronically.
Learn more about Third-Party Liability and Privacy Claims Coverage to understand how it fits within a broader business insurance strategy. Understanding what cyber insurance covers, especially in regards to third-party liabilities, is a crucial step in protecting your business in today's digital age.
5. Regulatory Fines and Penalties Coverage: Navigating the Complex World of Compliance
In today's interconnected world, data breaches and cyberattacks are a constant threat. But beyond the immediate costs of incident response and recovery, businesses also face a growing web of regulatory requirements surrounding data protection and cybersecurity. Failing to comply can result in hefty fines, penalties, and sanctions imposed by regulatory bodies. This is where regulatory fines and penalties coverage, a crucial component of a comprehensive cyber insurance policy, comes into play. If you're asking "what does cyber insurance cover?", this type of protection deserves careful consideration.
Regulatory fines and penalties coverage addresses the financial repercussions of non-compliance following a cyber incident or privacy violation. It helps businesses navigate complex regulatory landscapes across multiple jurisdictions, providing a financial safety net and expert guidance during challenging times. This coverage is increasingly important as governments worldwide strengthen data protection laws and enforcement mechanisms.
How it Works:
This type of coverage typically operates on a claims-made basis, meaning the policy must be active when the claim is made, regardless of when the incident occurred. After a cyber incident or privacy breach that triggers a regulatory investigation, the insured business notifies the insurer. The insurer then assesses the claim, considering the nature of the violation, applicable regulations, and the potential fines and penalties. If the claim is valid, the insurer covers the costs associated with regulatory proceedings, including:
- Regulatory fine and penalty payment: The core benefit is the payment of fines and penalties imposed by regulatory authorities.
- Legal representation during regulatory proceedings: The insurer typically provides access to legal counsel specializing in regulatory defense.
- Compliance consultation services: Expert advice and support can be provided to help businesses understand and address compliance gaps.
- Multi-jurisdictional coverage: For businesses operating globally, this ensures coverage across different regulatory frameworks.
- PCI DSS fine coverage: This covers fines specifically related to violations of the Payment Card Industry Data Security Standard (PCI DSS).
- Professional response to regulatory inquiries: Assistance is provided in responding to inquiries and investigations from regulatory bodies.
Examples of Successful Implementation:
While specific cases where insurance covered fines are often confidential, the scale of potential penalties is illustrated by public examples. British Airways was fined $26 million by the UK Information Commissioner's Office (ICO) under GDPR for a data breach. Marriott received a $124 million GDPR fine (later reduced to $23.8 million). H&M was fined $41 million for employee data processing violations. These examples highlight the significant financial risk associated with regulatory non-compliance. While insurance might not cover the entire amount in every case, it can significantly mitigate the impact.
Pros:
- Protection against escalating regulatory penalties: Fines can be substantial, crippling smaller businesses. This coverage provides crucial financial protection.
- Expert guidance through complex regulatory processes: Navigating regulatory investigations can be daunting. This coverage provides access to experienced legal and compliance professionals.
- Coverage across multiple regulatory frameworks: Businesses operating in different jurisdictions benefit from consistent coverage.
- Reduces the financial impact of compliance failures: It provides a financial cushion, allowing businesses to focus on remediation and recovery.
Cons:
- Some jurisdictions prohibit insurance coverage for fines: Certain types of fines, particularly those deemed punitive, may not be insurable in some regions.
- Excludes fines for intentional violations: Coverage typically doesn't apply to fines resulting from willful misconduct or gross negligence.
- Coverage limits may be insufficient for major violations: Businesses should carefully assess their coverage limits in relation to potential fines in their industry.
- Requires prompt notification and cooperation with the insurer: Timely reporting and full cooperation are essential for successful claims.
Tips for Businesses:
- Understand regulatory requirements in all operating jurisdictions: Thorough due diligence is crucial for compliance.
- Implement comprehensive data governance programs: Strong data governance practices reduce the risk of violations.
- Maintain detailed compliance documentation: This is crucial for demonstrating compliance during regulatory investigations.
- Consider separate coverage for PCI DSS and other industry-specific regulations: Specialized coverage may be necessary for certain industries.
Regulatory fines and penalties coverage is not just a nice-to-have; it's becoming a necessity for businesses of all sizes. When considering what does cyber insurance cover, remember that protecting your business from the financial fallout of regulatory action is just as important as protecting your data. This type of coverage offers vital financial protection and expert guidance, allowing businesses to navigate the increasingly complex world of data protection and cybersecurity compliance with greater confidence.
6. Cyber Crime and Funds Transfer Fraud Coverage
In today's interconnected world, financial transactions occur predominantly through digital channels. This reliance on technology, while offering convenience and efficiency, exposes businesses and individuals to a growing threat: cyber crime and funds transfer fraud. This type of fraud goes beyond simple data breaches and focuses specifically on schemes designed to steal money or assets. That's why, when asking "what does cyber insurance cover," it's critical to understand the protection offered against these increasingly sophisticated financial cyber crimes. This coverage can be a crucial safety net, mitigating the potentially devastating financial losses that can result from such attacks.
Cyber crime and funds transfer fraud coverage is a specialized component of a comprehensive cyber insurance policy. It addresses the unique risks associated with digital financial transactions and the manipulation of payment systems. This type of coverage acknowledges that modern cyber criminals often employ sophisticated tactics to exploit human vulnerabilities and bypass traditional security measures.
This coverage protects against several specific types of financial fraud, including:
- Social engineering attacks: These attacks manipulate individuals into divulging sensitive information or performing actions that benefit the attacker, such as transferring funds or providing access credentials. This can include phishing emails, impersonation scams, and pretexting.
- Fraudulent funds transfers: This involves unauthorized transfers of money from a victim's account to the attacker's account, often through compromised online banking credentials or manipulated payment instructions.
- Invoice and vendor payment fraud: Criminals may impersonate legitimate vendors and request payment to fraudulent accounts or alter existing invoices to redirect funds.
- Business email compromise (BEC): This sophisticated scam targets businesses by compromising email accounts of key personnel, such as executives or finance staff, to initiate fraudulent wire transfers or payments.
- Cryptocurrency theft: With the rise of cryptocurrency, thieves are increasingly targeting digital wallets and exchanges to steal virtual assets. This coverage can help recoup some of those losses.
- Telephonic fraud: This includes scams where criminals impersonate bank officials or other trusted entities to trick individuals into revealing financial information or authorizing transactions over the phone.
The benefits of having this coverage are significant. It helps businesses and individuals recover from the financial fallout of these attacks, which can be substantial. Real-world examples demonstrate the devastating impact of these crimes: Ubiquiti Networks lost $46.7 million to a BEC scam in 2018, while FACC aerospace company lost $61 million to a CEO fraud scheme. Even the sophisticated financial world isn't immune, as seen with Levitas Capital's $36 million loss in cryptocurrency theft. This coverage offers a crucial financial safety net, providing rapid response and support in these time-sensitive situations. It also addresses the often overlooked human element, recognizing that even well-trained employees can fall victim to sophisticated social engineering tactics.
However, this coverage isn't without its limitations. Insurers often require strong internal controls and security measures to qualify for coverage. There may be strict time limits for reporting incidents, and losses stemming from inadequate verification procedures might be excluded. Furthermore, coverage limits for this specific type of fraud might be lower than other cyber coverages.
To minimize your risk and potentially improve your eligibility for this coverage, consider implementing the following best practices:
- Multi-factor authentication: Implement MFA for all financial transactions and sensitive accounts.
- Dual approval processes: Establish dual approval processes for large fund transfers and critical payment changes.
- Employee training: Regularly train employees to recognize and avoid social engineering tactics.
- Independent verification: Verify all payment change requests through independent communication channels, never relying solely on email.
Cyber crime and funds transfer fraud coverage deserves a prominent place in any comprehensive cyber insurance policy because it directly addresses the increasing threat of financially motivated cyber attacks. For homeowners, businesses, high-net-worth individuals, and anyone conducting financial transactions online, this coverage provides crucial protection in an increasingly complex and dangerous digital landscape. By understanding the features, benefits, and limitations of this coverage, you can make informed decisions to protect your financial well-being in the face of evolving cyber threats.
7. Network Security and Privacy Liability Coverage
When considering what cyber insurance covers, Network Security and Privacy Liability Coverage is a critical component, especially for businesses and individuals with a significant online presence. This coverage addresses the financial fallout from security breaches and system failures that expose sensitive data or disrupt operations. In today's interconnected world, a single vulnerability can have cascading effects, leading to substantial legal and financial repercussions. This type of coverage is designed to protect you from those repercussions. It's particularly crucial in a landscape where cyber threats are constantly evolving and becoming more sophisticated.
Network Security and Privacy Liability Coverage essentially acts as a safety net when your digital defenses fail. It responds to incidents where your network security is compromised, leading to unauthorized access, data breaches, or the spread of malicious software. This could involve anything from a hacker gaining access to your customer database to a ransomware attack crippling your entire system. It also addresses liabilities stemming from inadequate security measures, system vulnerabilities, and the unintentional transmission of malware to third parties. This means that even if you weren't directly responsible for the initial attack, but your system played a role in its propagation, you could still be protected.
This coverage typically encompasses several key features:
- Network security failure liability coverage: This protects against claims arising from failures in your network security, such as inadequate firewalls or intrusion detection systems.
- Malware transmission liability protection: This covers situations where malware is inadvertently transmitted from your systems to third parties, even if you were unaware of its presence.
- Unauthorized access claim coverage: Provides protection against claims resulting from unauthorized access to your systems, leading to data breaches or other damages.
- System vulnerability exploitation coverage: Covers liabilities arising from the exploitation of known vulnerabilities in your systems, provided you weren't aware of the vulnerability and hadn't neglected to apply available patches.
- Denial of service attack liability: Protects against claims arising from denial-of-service attacks that disrupt your services and cause financial losses to your business or clients.
- Website defacement and alteration coverage: Provides coverage if your website is defaced or altered by unauthorized individuals, potentially damaging your reputation and causing business interruption.
Pros of Network Security and Privacy Liability Coverage:
- Comprehensive protection for network-related liabilities: This coverage offers broad protection against a wide array of cyber threats and vulnerabilities.
- Covers both active and passive security failures: Protects against both deliberate attacks and unintentional security lapses.
- Includes coverage for inadvertent malware transmission: Provides coverage even if you unknowingly spread malware.
- Addresses modern attack vectors and vulnerabilities: Adapts to the evolving cyber landscape and covers emerging threats.
Cons of Network Security and Privacy Liability Coverage:
- Requires maintenance of reasonable security standards: To qualify for coverage, you must demonstrate that you have implemented reasonable security measures.
- Excludes liabilities from known, unpatched vulnerabilities: If you fail to patch known vulnerabilities, you may not be covered for resulting damages.
- May have sublimits for specific types of network failures: Certain types of incidents may have lower coverage limits than others.
- Prior acts coverage may be limited: Coverage for incidents that occurred before the policy inception date may be restricted.
Real-World Examples:
Several high-profile cases highlight the importance of this coverage. SolarWinds faced numerous lawsuits following a devastating supply chain attack, and Kaseya customers sued the company after ransomware spread through its managed services platform. Similarly, CloudFlare faced potential liability claims during widespread outages. These examples underscore the significant financial and legal risks associated with network security failures.
Actionable Tips:
- Maintain current security patches and updates: Regularly update your software and systems to patch known vulnerabilities.
- Implement comprehensive network monitoring and intrusion detection: Invest in robust security tools to detect and respond to threats in real-time.
- Document security policies and incident response procedures: Develop clear procedures for handling security incidents and ensure all employees are aware of them.
- Regularly conduct vulnerability assessments and penetration testing: Proactively identify and address vulnerabilities in your systems.
Network Security and Privacy Liability Coverage deserves a prominent place on any list addressing "what does cyber insurance cover" because it tackles a crucial aspect of modern risk management. In an increasingly interconnected world, network security failures can have devastating consequences. This coverage provides essential protection against the financial and legal ramifications of these incidents, helping businesses and individuals recover from cyberattacks and maintain their operations. By understanding the features, benefits, and limitations of this coverage, you can make informed decisions about your cyber insurance needs and protect yourself from the ever-evolving threats in the digital landscape.
7 Key Coverage Aspects Compared
| Coverage Type | Implementation Complexity 🔄 | Resource Requirements ⚡ | Expected Outcomes 📊 | Ideal Use Cases 💡 | Key Advantages ⭐ |
|---|---|---|---|---|---|
| Data Breach Response and Notification | Moderate – requires coordination with legal, PR, and forensic teams | Medium – forensic, legal, PR services | Rapid incident response, regulatory compliance, reputational protection | Companies handling sensitive personal data, regulated industries | Comprehensive breach support, ensures compliance, reputation management |
| Business Interruption and System Downtime | High – involves detailed financial tracking and operational planning | High – finance, IT, disaster recovery | Compensation for lost revenue, supports business continuity | Businesses reliant on continuous operations, e-commerce, manufacturing | Maintains cash flow, covers direct/indirect losses, supports recovery efforts |
| Ransomware and Cyber Extortion | High – requires specialized negotiation and payment protocols | Medium to High – negotiation teams, backups | Faster resolution of ransomware attacks, minimized operational impact | Organizations at risk of ransomware, with critical data dependency | Access to expert negotiators, reduces downtime, professional payment guidance |
| Third-Party Liability and Privacy Claims | Moderate – legal coordination and claims management | Medium – legal defense, regulatory expertise | Legal defense and settlements protection, regulatory defense | Businesses with large customer bases or sensitive third-party data | Comprehensive legal protection, covers lawsuits and regulatory claims |
| Regulatory Fines and Penalties | Moderate – compliance monitoring and legal support | Medium – legal, compliance consultation | Financial protection from fines, regulatory guidance | Companies in regulated sectors with multi-jurisdictional exposure | Expert regulatory navigation, reduces financial impact, multi-jurisdictional |
| Cyber Crime and Funds Transfer Fraud | High – controls and verification protocols required | Medium – fraud prevention, IT controls | Protection against financial cyber crimes and frauds | Organizations exposed to financial transactions and social engineering | Covers sophisticated frauds, rapid response, includes emerging threats |
| Network Security and Privacy Liability | Moderate to High – requires ongoing security management | Medium – IT security, monitoring systems | Protection against network security breach liabilities | Businesses exposed to network vulnerabilities, service providers | Covers malware transmission, unauthorized access claims, modern attack vectors |
Securing Your Future: Making Informed Cyber Insurance Decisions
Understanding what cyber insurance covers is crucial in today's digital landscape. This article explored seven key areas of coverage, from data breach response and notification to regulatory fines and penalties, offering a comprehensive overview of how cyber insurance can protect individuals, families, and businesses from the devastating impact of cyberattacks. We’ve highlighted the importance of coverage for business interruption and system downtime resulting from incidents like ransomware and cyber extortion. We also explored the critical role of third-party liability and privacy claims coverage, as well as protection against cybercrime and funds transfer fraud. Finally, we examined network security and privacy liability coverage, providing a holistic picture of what cyber insurance covers.
Mastering these concepts allows you to proactively safeguard your personal and professional life against evolving cyber threats. Whether you're a homeowner concerned about personal data breaches, a high-net-worth individual managing complex digital assets, a business owner protecting sensitive client information, or a professional navigating liability risks, the right cyber insurance policy can provide much-needed peace of mind. The potential financial and reputational damage from a cyber incident can be catastrophic, but understanding what cyber insurance covers and selecting appropriate coverage can significantly mitigate these risks.
For a tailored approach to understanding what cyber insurance covers and securing the best protection for your unique needs, Wexford Insurance Solutions offers expert guidance and comprehensive cyber insurance solutions. Visit Wexford Insurance Solutions today to learn how our personalized approach can help fortify your cyber defenses and protect your future.
 Cyber Security Insurance For Small Business: Complete Guide
Cyber Security Insurance For Small Business: Complete Guide Cyber Liability Insurance Cost: Protect Your Business Today
Cyber Liability Insurance Cost: Protect Your Business Today