Think of a data breach response plan as your company’s fire escape plan. It's the documented strategy you'll turn to when a security incident hits, guiding your team through the chaos. This isn't just a technical document; it's a critical roadmap that defines key roles, communication protocols, and containment procedures to stop the bleeding and minimize the damage.
Why a Data Breach Response Plan Is Non-Negotiable
When a breach happens, the business can grind to a halt. It's not just about some abstract financial cost—it's about the very real, tangible chaos that erupts when your team is caught completely off guard. Without a plan, you're just reacting on instinct, and in a crisis, instinct often leads to expensive mistakes.
Picture this: your customer service lines are blowing up with angry clients, all while your IT team is just trying to figure out what happened and how bad it is. At the same time, your leadership is forced to make huge decisions with spotty information. This isn't a hypothetical; it's the reality for unprepared businesses.
The Real-World Fallout of Inaction
The damage goes far beyond the immediate disruption. The erosion of customer trust can be swift and brutal. Once that trust is gone, it's incredibly difficult to earn back, leading to long-term reputational harm that can haunt your brand for years. A slow or fumbled response tells your customers and partners one thing: you don't take their security seriously.
The scale of this problem is staggering. Since 2004, approximately 23.1 billion user accounts have been exposed in data breaches worldwide. This has impacted about 7.7 billion unique email addresses, which means the average online user has had their identity compromised about three times. These numbers make it crystal clear—it’s not a matter of if a breach will happen, but when.
A data breach response plan is what moves your organization from a state of reactive panic to one of proactive control. It’s not just a document to satisfy compliance; it’s a fundamental investment in your company’s resilience and survival.
Beyond Response to Prevention and Resilience
Thinking about a breach only in terms of response is shortsighted. To truly appreciate why a plan is so critical, you have to consider prevention, too. For example, learning how to prevent data breaches in virtual meetings is a proactive measure that strengthens your security from the ground up.
Ultimately, your response plan is just one piece of a larger business continuity puzzle. Having the right insurance coverage is another essential layer. Looking into options like business continuity insurance can provide a financial safety net, giving you the breathing room to focus on recovery without staring down financial ruin.
Building Your Incident Response Team
A data breach response plan is only as good as the people executing it. When a crisis hits, you simply won’t have time to debate who’s in charge of what. Pre-defining roles and responsibilities is what separates a controlled, effective response from absolute chaos.
Think of your response team as a dedicated emergency crew. Each person has a specific, vital role, and they must work together seamlessly under immense pressure. This isn't just an IT problem; it's a business-wide challenge that demands a cross-functional team with the authority to act decisively. If you want a deeper dive into the mechanics of a full-scale response, it's worth reviewing a comprehensive guide on Data Breach Incident Response to see how all the pieces fit together.
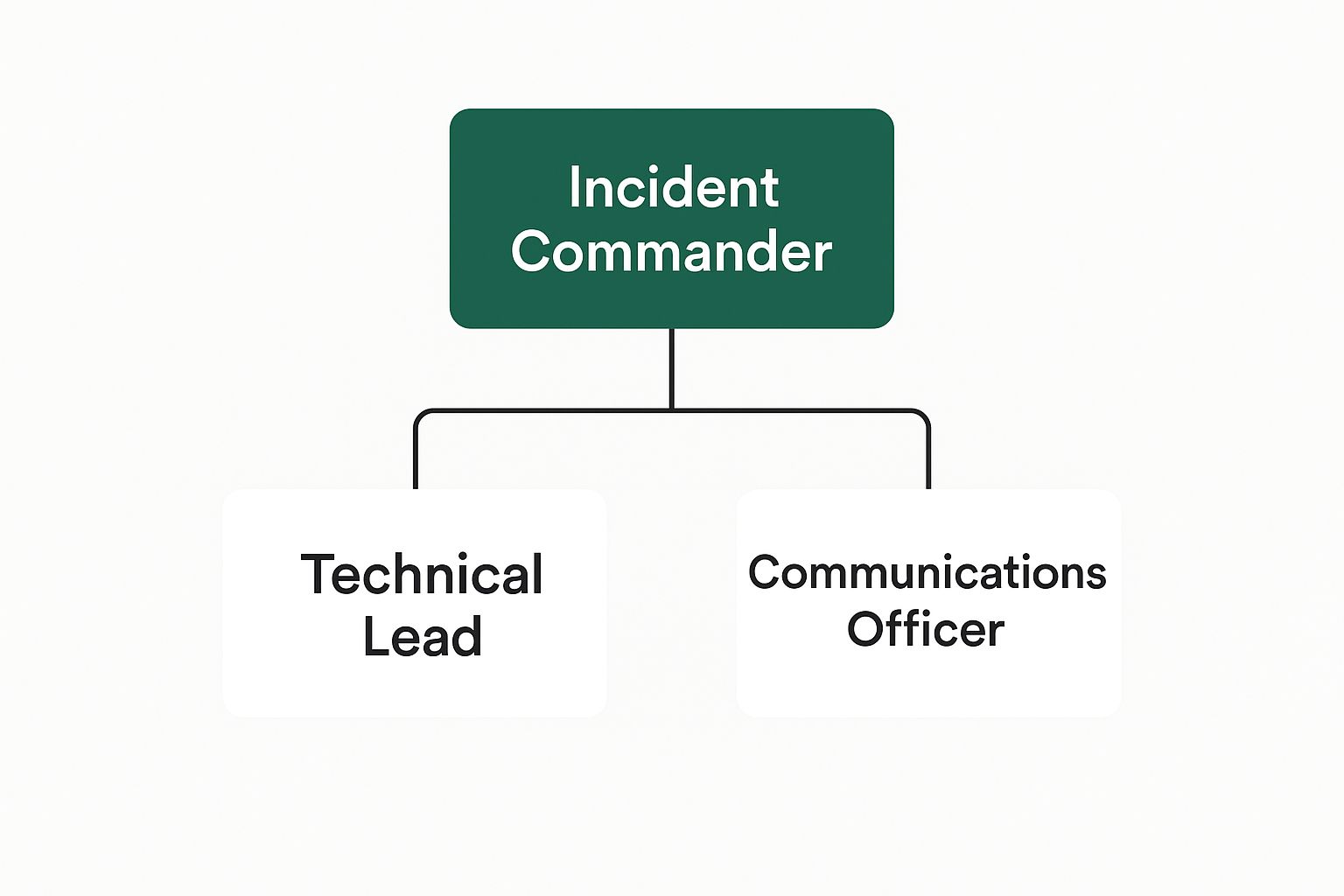
This diagram illustrates a straightforward command structure that keeps the response organized and focused.
As you can see, having a clear chain of command is crucial. An Incident Commander sits at the top, directing both the technical and communication arms of the response to ensure everyone is working from the same playbook.
Assembling Your Core Players
One of the biggest mistakes I see is businesses assuming the IT department can handle a breach on its own. While their technical skills are indispensable, a major incident ripples through every part of the organization. Your team needs to be a hand-picked group of leaders who can manage the fallout from their unique perspectives.
At a minimum, your core team should include:
- Executive Leadership: They're there to make the big calls, approve necessary spending, and be the final point of authority.
- IT and Security: These are your boots on the ground. They lead the technical investigation, work to contain the threat, and get your systems back online.
- Legal and Compliance: This isn't just about advice. They're actively navigating a minefield of notification laws (like GDPR or CCPA), managing legal liability, and signing off on all public statements.
- Public Relations/Communications: Their job is to protect the company's reputation by managing the narrative. They handle all messaging, both internally to staff and externally to customers and the media.
- Human Resources: HR steps in to manage all employee-related concerns, from communicating with staff whose data may have been exposed to handling internal anxieties.
Expert Tip: Having these roles—and their backups—identified before a crisis is the single most critical preparation you can make. The middle of an emergency is the worst possible time for introductions.
Defining Roles and Responsibilities
Giving someone a title isn't enough. Every person on the team needs a crystal-clear charter that spells out their exact duties during an incident. For example, the legal expert isn't just on standby; they’re the one who determines if a 72-hour notification clock has officially started ticking. The PR lead isn’t just winging it; they’re drafting statements based only on verified facts from the technical lead, not on rumors or speculation.
To make this concrete, your plan should include a roles and responsibilities matrix. It clearly defines who does what, removing ambiguity when every second counts.
Key Roles in Your Data Breach Response Team
This table breaks down the essential members of an incident response team, their core duties during a breach, and the expertise they need to bring to the table.
| Role | Primary Responsibilities | Essential Skills |
|---|---|---|
| Incident Commander | Oversees the entire response, coordinates all team efforts, and reports directly to executive leadership. | Decisive leadership, clear communication, and the ability to stay calm under intense pressure. |
| Technical Lead | Manages hands-on containment, eradication, and recovery. Also responsible for preserving forensic evidence. | Deep technical security knowledge, system administration skills, and analytical problem-solving abilities. |
| Communications Officer | Develops and executes the communication strategy for all stakeholders (customers, media, employees). | Crisis communication experience, strong writing skills, and established media relations expertise. |
| Legal Counsel | Ensures all actions comply with relevant data protection laws and regulations. Manages legal risk and liability. | Expertise in data privacy law (e.g., GDPR, CCPA), regulatory requirements, and corporate liability. |
By building out this team and clearly defining each person's function, you're laying the foundational stone for a resilient plan that can actually withstand the storm of a real-world data breach.
Executing Immediate Containment and Eradication
The moment your incident response team confirms a breach, the clock is on. Your first moves are everything, and they will absolutely set the tone for the entire recovery process. Panic is the enemy; a methodical, pre-planned approach is your best friend.
This isn’t the time for a big meeting to figure out what to do. Your data breach response plan should have already laid out these immediate actions. The goals are simple but critical: stop the intruder from doing more damage and kick them out of your systems for good.
Here's where I see a lot of inexperienced teams go wrong: they just pull the plug on everything. That kind of chaotic shutdown can destroy crucial forensic evidence, making it impossible to figure out how they got in or what they took. Instead, your focus needs to be on strategic isolation.
The Art of Strategic Isolation
Think of containment like closing fire doors in a burning building. You’re trapping the fire in one area to save the rest of the structure. On a network, this means carefully isolating the compromised systems from everything else.
This might look like:
- Network Segmentation: Taking the compromised part of your network offline from the rest of the company.
- Cutting Off Remote Access: Immediately revoking VPN access for any suspicious accounts.
- Forcing Credential Resets: Making everyone change their passwords on critical systems, starting with your admins and service accounts.
Precision is the name of the game. You're trying to surgically remove the threat's access while causing as little disruption to business as possible. This is where having a clear map of your critical assets really pays off—you’ll know exactly which systems to lock down first to protect your crown jewels.
A quick but crucial tip: Preserving evidence is just as important as stopping the attack. Every action taken during containment must be meticulously documented. Your tech team should be taking copies of server logs, disk images, and network traffic data. This evidence is vital for both your internal investigation and for any legal or regulatory follow-up.
Moving from Containment to Eradication
Once the incident is contained and you're confident the attacker can't move around your network anymore, it's time to start kicking them out. This is the eradication phase, where you actively remove the threat from your environment.
The exact process really depends on the type of attack you're dealing with, but the playbook usually includes these moves:
- Removing Malware: Using trusted security tools to scrub infected systems and endpoints clean.
- Disabling Breached Accounts: Not just changing passwords, but completely disabling any user accounts that were compromised.
- Patching Vulnerabilities: Finding and immediately patching the security hole the attacker exploited to get in.
This phase isn't just about the technical cleanup; it's also about watching the clock on downtime. The costs can escalate quickly. To get ahead of this, it's smart to understand the factors influencing business interruption insurance cost as part of your larger risk management strategy.
Finally, remember that recovery isn't a race. It's a deliberate, careful process of restoring systems from clean, verified backups. Before any system comes back online, it needs to be hardened and monitored to ensure the threat is truly gone. Rushing this step is the fastest way to get reinfected and end up right back where you started. Your data breach response plan needs to mandate this phased approach for a real recovery.
Navigating Communications and Legal Obligations
https://www.youtube.com/embed/SC7IR_XVZvs
Once you’ve stopped the bleeding and contained the breach, you step into what is often the most treacherous part of the entire ordeal: managing communications.
How you talk about the incident—to your customers, your team, and the regulators—will either start the healing process or burn whatever trust you have left to the ground. This isn't about just firing off a quick apology email. It’s a delicate, high-stakes operation with massive legal and reputational fallout if you get it wrong.
Your data breach response plan absolutely must have a section dedicated to this. It needs to spell out who gets told what, and when. This is where your legal counsel stops being a consultant and becomes one of the most critical players on your response team. They’re the ones who will guide you through the dizzying maze of notification laws.
Getting a Handle on Your Legal Duties
Let's be clear: there is no single rule for breach notification. The regulations are a messy patchwork that varies wildly by location and industry.
The GDPR in Europe, for instance, is famous for its strict 72-hour notification deadline, which starts ticking the moment you even suspect a breach. In the U.S., it's even more complicated, with a jumble of different state laws. A slip-up here doesn’t just look bad; it can lead to crippling fines and years of legal headaches.
Your plan needs a well-defined process for immediately looping in your legal experts. Their first job is to figure out which specific regulations apply based on the data that was stolen. That analysis will dictate your entire communication timeline.
One of the worst things I see companies do is wait to notify because they're afraid of the backlash. I get it, but transparency, even when the news is awful, is almost always the better long-term play. Delaying just makes you look guilty and gives people the impression you have something to hide.
This part of the process breaks down into a few critical actions:
- Pinpoint Who Was Affected: You need to know precisely whose data was compromised—customers, employees, business partners, or all of the above.
- Assess the Regulatory Impact: Which laws have you triggered? CCPA in California? HIPAA for healthcare data? GDPR for European citizens? Your legal team will determine the scope.
- Set Hard Deadlines: Based on the regulations, work with counsel to establish an unbreakable timeline for notifying official bodies and the people affected.
Crafting a Message That’s Clear and Human
While the lawyers are focused on compliance, your communications lead needs to focus on the human side of the crisis. The messages you send out must be direct, empathetic, and free of confusing jargon or corporate doublespeak. People are scared and angry; they need straight answers.
Your public statements and individual notifications should cover four key things:
- What happened: Give a simple, factual account of the incident.
- What information was involved: Be specific about the types of data exposed (e.g., names, email addresses, credit card information).
- What you're doing now: Explain the steps you’ve already taken to lock down your systems and how you plan to help those affected.
- What they should do: Offer clear, actionable advice so they can protect themselves, like changing passwords or placing a fraud alert on their credit.
Breaches happen to everyone, and the response has to fit the situation. We’ve seen massive incidents like Oracle Cloud losing 6 million records and the Iranian financial institution Bank Sepah exposing over 42 million customer files. These examples, which you can read more about at BrightDefense.com, show how different the playbook can be depending on the industry and the sensitivity of the data.
A solid insurance policy is also a lifesaver at this stage. Having the right coverage can make or break your ability to manage the financial side of the response. To get a better sense of what's involved, take a look at our guide on cyber security insurance for small business. It’s a great starting point for understanding how insurance can provide a crucial financial backstop when you need it most.
Shifting from Recovery to Reinforcement
Once you've contained a data breach, it’s tempting to breathe a sigh of relief. But the mission isn't over. In my experience, what you do after the immediate threat is neutralized is what truly separates a resilient organization from a future victim.
This post-incident phase is your golden opportunity. It’s a chance to turn a painful, costly event into a powerful catalyst for change. We're not just talking about getting back to "business as usual." The goal is to emerge from this stronger and smarter than you were before. To do that, you have to dig deep with a post-mortem analysis that goes far beyond just patching the hole the attacker used.
Asking the Tough Questions
A blame-free post-mortem is the only kind that works. The focus has to be on relentless, honest curiosity. Your incident response team needs to shift gears from firefighting to investigation, asking the hard questions that lead to real insights.
Here’s what you need to be asking:
- The How: How exactly did they get in? Was it a clever phishing email that someone clicked? An unpatched server sitting forgotten? Or maybe credentials bought on the dark web? Get specific.
- The Why: Which of our security tools failed us? Did the firewall rules have a gap? Did our endpoint protection somehow miss the malware? Why didn't the controls we paid for actually work?
- The When: How long were they inside our network before we noticed? Pinpointing this detection gap is crucial for understanding how much damage could have been done.
The answers to these questions are your roadmap. If a phishing email was the culprit, the fix isn't just deleting it. It's about strengthening email filters, yes, but also about overhauling your security awareness training so your team can spot these threats themselves.
A post-incident review isn't about pointing fingers. It's about finding the cracks in your foundation. A successful review turns lessons learned into concrete security upgrades, making sure your data breach response plan gets better with every real-world test.
Turning Lessons Into Action
With the answers in hand, it's time to act. This is where your recovery work blends directly into your long-term security strategy. You take the findings from your review and build a stronger fortress.
For example, if stolen credentials were the key, then rolling out multi-factor authentication (MFA) across every critical system is no longer a "nice-to-have"—it's an immediate priority. If an old, unsupported application was the weak link, you need a plan to either upgrade it or rip it out and replace it. Now.
The financial motivation to be this thorough is staggering. The global average cost of a data breach has already hit $4.88 million. Worse, some projections show that the annual cost of cybercrime could balloon to an incredible $10.5 trillion by 2025. As highlighted in recent cybercrime statistics, these aren't just abstract numbers; they represent a real and present danger to your bottom line. You can explore more of these staggering financial risks at BDEmerson.com.
This recovery period is also the perfect time to review your financial safety nets. Take a hard look at your cyber liability insurance cost and make sure your coverage is actually aligned with the real-world threats you now know you face.
Frequently Asked Questions
When you're putting together a data breach response plan, some practical questions always come up. Getting these sorted out ahead of time is the key to building a plan that your team can actually use when the pressure is on.
How Often Should We Test Our Plan?
A data breach response plan can't just sit on a shelf gathering dust. Think of it as a living document. For it to work, you have to keep it sharp and relevant to how your business and the threats around you are changing.
The gold standard is to run through your plan with a tabletop exercise at least annually. This keeps the procedures fresh in everyone's minds. You'll also want to re-test the plan anytime something significant changes—like implementing a new IT system, a major team shuffle, or a shift in how you do business.
What Is the Biggest Mistake in a Breach Response?
I've seen it time and time again. In the frantic moments after a breach is discovered, the single most damaging mistake is delaying communication. It’s a natural instinct to want to get all the facts straight before going public, but this hesitation almost always makes things worse.
Waiting destroys the trust you’ve built with your customers. It can also land you in serious legal trouble, especially with regulations like GDPR that have very tight notification deadlines. Being upfront and honest, even when the news is bad, is always the better path to recovery.
Can Small Businesses Create an Effective Plan?
Absolutely. You don't need a Fortune 500 budget to build a solid data breach response plan. It’s not about having endless resources; it’s about having a clear, practical, and well-rehearsed strategy.
For a smaller company, a strong plan really comes down to a few core things:
- Who does what? Make sure roles are crystal clear, with backups for every key person.
- A simple call list: Everyone needs to know exactly who to contact and in what order.
- Ready-to-go messages: Having notification templates drafted in advance saves critical time.
- Your expert bench: Don't wait for a crisis to find cybersecurity and legal help. Have them on speed dial.
Nailing these fundamentals allows a small business to react with the speed and confidence of a much larger organization. And just as important is having the right financial safety net. Understanding the ins and outs of cyber security insurance for small business can give you the resources to handle the expensive aftermath of a breach.
Tackling cyber risk takes more than just a plan; it takes a partner who knows the landscape. At Wexford Insurance Solutions, we specialize in helping businesses like yours secure the right cyber liability coverage to protect what you’ve built. Secure your free consultation today and let's build a more resilient future together.
 What Is Full Coverage Car Insurance Explained
What Is Full Coverage Car Insurance Explained What Is Tail Coverage Insurance? A Practical Guide
What Is Tail Coverage Insurance? A Practical Guide