Cyber liability insurance is a unique type of policy that acts as your financial backstop after a data breach or other cyber attack. Think of it as a specialized emergency response team for your digital world. When a digital disaster strikes, this policy kicks in to cover the overwhelming costs, from recovering lost data and paying legal fees to handling steep regulatory fines.
What Exactly Is Cyber Liability Insurance?
Most businesses already have general liability insurance. It’s a must-have for handling physical-world problems, like a client slipping and falling on your premises. But what happens when the damage isn't physical? What if a hacker makes off with your entire customer database or a ransomware attack grinds your operations to a halt?
That's the dangerous gap where traditional insurance policies often fail. Your standard general liability or business owner's policy almost always excludes losses from digital incidents. Cyber liability insurance was created specifically to plug this critical hole in your coverage.
Why It's a Modern Business Necessity
In today's economy, data is currency. For many businesses, it's their most valuable asset, making its protection an absolute priority. This specialized coverage is no longer an optional extra; it's a core part of any smart risk management plan. And it’s not just for big tech companies—any organization that handles sensitive information is on a hacker's radar.
That includes everyday data like:
- Customer names, addresses, and payment card details
- Employee Social Security numbers and private records
- Protected Health Information (PHI) in a medical setting
- Sensitive client financial data held by law or accounting firms
To give you a clearer picture, here’s a quick breakdown of what this insurance does.
Cyber Liability Insurance At a Glance
| Key Function | What It Covers | Primary Benefit |
|---|---|---|
| Breach Response | Costs for notifying customers, credit monitoring, and PR crisis management. | Preserves customer trust and protects your brand reputation. |
| Financial Protection | Legal defense fees, settlements, regulatory fines, and extortion payments. | Prevents a cyber incident from causing a financial catastrophe. |
| Business Recovery | Costs to restore data, repair systems, and cover income lost during downtime. | Helps you get back on your feet and operational as quickly as possible. |
This table shows how the policy provides a multi-layered defense, addressing the immediate crisis while also managing the long-term financial fallout.
A single data breach can unleash a torrent of expenses. You're suddenly facing costs for forensic investigators to figure out what happened, a PR firm to manage the public fallout, and lawyers to defend you against inevitable lawsuits. For a small or medium-sized business, these costs could easily be a knockout blow.
The demand for this protection is skyrocketing right alongside the threats. While these policies first emerged in the late 1990s, they’ve become mainstream over the last decade. Considering the average cost of a U.S. data breach soared to $9.4 million in 2022, it's no surprise the cyber insurance market is expected to top $20 billion by 2025. You can read more about how these trends are shaping business insurance on our blog.
Just as you wouldn't run your business without insurance for fire or theft, you can no longer afford to leave your digital doors unlocked. Cyber liability insurance is an essential piece of your company's armor, working with other commercial insurance types to safeguard your future. It gives you the money and expert guidance you need to survive a cyber attack and get back to what you do best.
What’s Actually Inside a Cyber Insurance Policy?
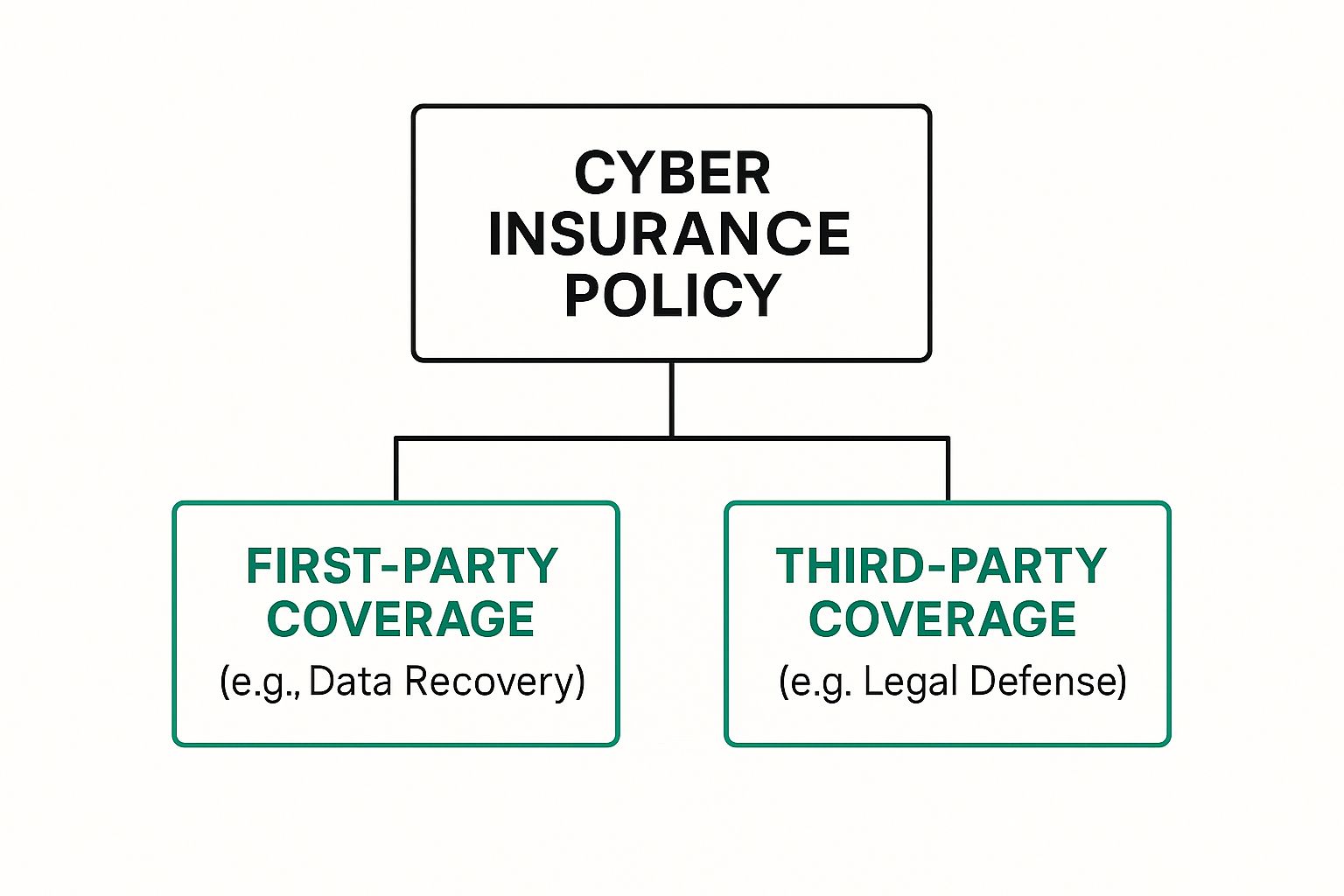
To really get what cyber liability insurance is, you have to pop the hood and look at the engine. On the surface, it’s a policy that helps with cyberattacks, but how it works is a different story. Think of it like this: if your business is a house that catches fire, you need money to rebuild your own walls, but you also need money if the fire spreads and damages your neighbor’s property.
A cyber policy works the same way, split into two fundamental parts: First-Party Coverage and Third-Party Coverage. Getting the hang of how these two work together is the key to understanding what your insurance will actually do when a crisis hits.
This diagram breaks down that structure, showing how a policy protects you from both internal costs and external liabilities.
As you can see, every protection falls into one of these two buckets, giving you a complete safety net for your business.
First-Party Coverage: Covering Your Own Costs
First-party coverage is your company’s financial first-aid kit. It’s designed to cover the immediate, direct expenses you face trying to get back on your feet after a cyber incident. When a hacker breaches your network, the first damage is to your systems, your data, and your ability to operate. This part of the policy is all about stopping the financial bleeding.
Here’s what you’ll typically find covered:
- IT Forensic Services: You need to figure out what happened, fast. This pays for the digital detectives who come in to investigate the breach, see what was stolen, and secure your network.
- Data Recovery and Restoration: If ransomware locks up your files or a virus wipes your server, this helps pay the experts needed to restore your data and get your software running again from backups.
- Business Interruption: This one is huge. If an attack shuts down your operations, this coverage reimburses you for the income you lose during that downtime, so you can still make payroll and pay the bills.
- Cyber Extortion and Ransomware: When you're facing a ransomware demand, this can cover the ransom payment itself and, just as importantly, the fees for professional negotiators who can often get the price down.
Real-World Scenario: A local accounting firm gets hit with ransomware two weeks before the tax deadline, locking up all their client files. Their business interruption coverage would compensate for the projected lost revenue from being unable to file returns, while the data recovery portion would pay to restore the systems.
Third-Party Coverage: Handling Claims From Others
While first-party coverage looks inward, third-party coverage looks outward. It’s your shield against the lawsuits and regulatory fines that come from others who were harmed by your security breach—think customers, partners, or government agencies. When their data is compromised on your watch, they’ll come looking for someone to blame.
This is your defense fund, and it usually includes:
- Liability and Legal Defense: This covers the staggering costs of hiring lawyers to defend you against lawsuits from customers whose private information was exposed. It pays for legal fees, court costs, and any settlements or judgments.
- Regulatory Fines and Penalties: If you handle sensitive data, you’re on the hook for regulations like HIPAA or PCI DSS. A breach can trigger massive fines from regulators, and this coverage helps pay them.
- Notification and Credit Monitoring Costs: After a breach, you’re legally required to notify everyone affected. This covers the cost of sending out those letters and offering credit monitoring services to help victims protect their identities.
For a closer look at these specific protections, our guide on what does cyber insurance cover goes into much greater detail. Understanding both sides of the policy is the only way to see the full picture of how it protects you when things go wrong.
Is Your Business a Target? Who Really Needs This Coverage?
It’s a persistent and dangerous myth that cybercriminals only have their sights set on massive, multinational corporations. The reality on the ground is much different. Hackers often see smaller businesses as the path of least resistance—softer targets with fewer security resources but just as much valuable data.
The truth is, if your business uses technology to store sensitive information, you're on the map. This includes customer names, payment details, employee records, or patient data. It’s not about the size of your company; it's about the value of the data you hold.
Many business owners feel their risk is low, but the numbers tell a different story. A staggering 43% of all cyber attacks target small businesses. This statistic reveals a critical vulnerability: the very businesses least equipped to handle the financial fallout are the ones frequently in the crosshairs.
Who Is Most at Risk?
While any business with a digital footprint has some level of risk, certain industries are practically magnets for cybercriminals because of the data they handle. If you operate in one of these sectors, the question isn’t if you need coverage, but how much.
Let's break down a few prime examples:
- Healthcare Providers: Medical clinics, dental offices, and therapists store Protected Health Information (PHI). A breach here can trigger devastating HIPAA fines that can easily run into six or seven figures, not to mention the costs of notifying patients and providing credit monitoring.
- Professional Services: Law firms, accounting practices, and consultants are treasure troves of sensitive client information. The reputational damage from a leak can be irreversible, shattering the client trust that is the absolute foundation of their business.
- Retail and E-commerce: Any business that processes credit card transactions is on the hook for protecting that data under PCI DSS standards. A breach can lead to steep non-compliance penalties and liability for fraudulent charges.
- Contractors and Trades: Even businesses that don't seem "tech-focused" are vulnerable. A contractor stores employee Social Security numbers for payroll and client banking details for payments—all of which are hot commodities on the dark web.
A Real-World Scenario
Abstract risks are easy to brush aside. To truly grasp why cyber liability insurance is so vital, it helps to see how an attack could play out for a business just like yours.
Imagine a local accounting firm with a dozen employees. A staff member, trying to clear their inbox, clicks on a phishing email. In an instant, ransomware spreads through their network, encrypting every single client's financial records right before a major tax deadline.
Without cyber insurance, the firm faces an impossible choice: pay a five-figure ransom with no guarantee of getting their data back, or tell their clients they’ve lost everything. The business interruption costs alone could bankrupt them in a matter of weeks.
This isn’t a far-fetched horror story; it happens every single day. A solid policy acts as a lifeline, giving you access to expert negotiators, covering the ransom if necessary, and reimbursing your lost income while you get back on your feet. Implementing strong 9 corporate governance best practices for SMBs is a key first step in spotting these operational risks before they turn into disasters.
Ultimately, protecting your business demands a proactive mindset. Understanding your vulnerabilities is the first step in a complete cyber security risk management strategy, where insurance serves as your ultimate financial safety net. Every business owner needs to take an honest look at the data they handle and accept that in today's world, every company is a tech company—and therefore, a target.
Navigating the Fine Print: Policy Exclusions to Watch For
Figuring out what a cyber liability policy covers is only half the battle. The real trick is knowing what it doesn't cover. Insurance policies are contracts, full of specific limitations, and if you overlook them, you could be in for a nasty surprise right when you need help the most.
Think of your policy as a highly specialized security guard for your digital assets. They’re an expert at handling things like data breaches and ransomware, but they aren't going to fix a leaky pipe or a broken window. Understanding their exact job description—including what’s not on the list—is absolutely critical.
Every policy is a bit different, but most have a set of common exclusions you need to be on the lookout for. These aren't hidden traps. They're simply the boundaries that define the relationship between you and the insurer, making it clear where their responsibility ends and yours begins.
Understanding Common Policy Exclusions
You have to sit down and actually read your policy documents. That said, some exclusions pop up so often you can pretty much count on seeing them. Let’s walk through the big ones that trip up business owners all the time.
Here are a few key limitations you'll almost certainly find:
- Prior Acts or Known Breaches: This one’s straightforward. Your policy won't cover any cyber incident that was already in progress or happened before your coverage started. You can't buy insurance for a house that's already on fire.
- Failure to Maintain Security Standards: This is a huge one. If you don't implement basic, reasonable security measures—like keeping your antivirus software updated or installing a critical security patch—your claim could be denied. Insurers see this as leaving the front door unlocked and then being surprised when you get robbed.
- Bodily Injury and Property Damage: Cyber policies are designed for digital and financial fallout. If a hacker takes over a piece of equipment and it physically injures an employee or smashes into a wall, that's a job for your general liability or property insurance, not your cyber policy.
- Acts of War or Terrorism: Most policies have clauses that exclude damage from major, state-sponsored cyberattacks or events officially classified as acts of war. The language here can get very technical, and it’s often a major point of discussion.
The key takeaway here is simple: cyber insurance is not a replacement for good security practices. It’s a financial backstop meant to work alongside your own efforts, not as a substitute for them.
So, what's the difference between what a cyber policy covers versus a traditional business policy? It can get confusing, but the distinction is crucial.
Cyber Insurance vs General Liability: A Clear Comparison
This table breaks down how each policy type typically responds to different kinds of incidents, highlighting the gaps that a general liability policy leaves wide open.
| Incident Type | Covered by Cyber Liability? | Covered by General Liability? |
|---|---|---|
| Customer data breach (PII leak) | Yes | No |
| Ransomware attack & extortion fees | Yes | No |
| Business interruption from a hack | Yes | No |
| Phishing email leads to fund transfer | Yes | No |
| Physical injury from a slip-and-fall | No | Yes |
| Damage to your office from a fire | No | Yes |
As you can see, these policies are designed for completely different worlds. One protects your digital life, the other your physical one. Relying on just one leaves your business dangerously exposed.
Your Responsibilities as a Policyholder
This brings us to a critical point: your policy is a partnership. The insurance company agrees to cover your financial losses from a cyberattack, and in return, you agree to maintain a reasonable security posture. If you don't hold up your end of the deal, often called a "failure to maintain" condition, you could void your coverage entirely.
For example, if your insurer's application required you to have multi-factor authentication (MFA) on all critical accounts and you never got around to setting it up, they would have clear grounds to deny a claim that resulted from a simple password theft. Taking the time to understand these conditions isn't optional. To get more comfortable with this, it’s worth learning more about how to read an insurance policy so you can spot these requirements.
Ultimately, digging into the fine print is about preventing a painful misunderstanding later. When you know the boundaries of your coverage from day one, you can set realistic expectations and make sure you’ve put the right protections in place—both with your insurance and your own security habits.
How Your Cyber Insurance Premium Is Calculated
When an insurance company quotes you a price for a cyber liability policy, that number isn't pulled out of a hat. It’s the result of a deep dive into your business's risk profile, not unlike how home insurance carriers look at a house's location and age before writing a policy.
For cyber insurance, the underwriters are your digital risk assessors. They’re trying to answer one fundamental question: how big of a target are you, and how well are you defended? The premium you're quoted is a direct reflection of their answer. A business with rock-solid security and a small data footprint will always get a better rate than a company with leaky defenses that's sitting on a mountain of sensitive files.
The good news? This process puts you in the driver's seat. Once you understand what drives your premium, you can take concrete steps to lower it. Beefing up your security isn't just about stopping attacks—it's about making your business a more attractive, less risky client for any insurer.
Key Factors That Influence Your Premium
Insurers essentially look at your business from two angles. Think of it as two sides of a coin: on one side is what you have to protect, and on the other is how well you're protecting it.
Here’s what they’re sizing up:
- Your Industry: Let's be honest, some fields are just riskier than others. A healthcare clinic managing patient records under HIPAA faces a world of regulatory pain that a small construction firm doesn't. That's why industries like healthcare, finance, and legal services often see higher premiums—the data they handle is simply more valuable and more regulated.
- Company Size and Revenue: It's a simple calculation. Larger businesses with higher revenues have more to lose from downtime and are juicier targets for cybercriminals. This naturally translates to higher potential claim costs and, therefore, a higher premium.
- Data Sensitivity and Volume: The type and amount of data you manage are huge factors. A business storing 100,000 credit card numbers is in a completely different risk category than one that only collects email addresses for a monthly newsletter. The more personal and financial data you hold, the higher your risk.
The Power of a Strong Security Posture
While you can't change your industry, you have total control over the single biggest factor in your premium calculation: your cybersecurity hygiene. This is where you can really make a difference in your annual cost. Insurers look at strong security controls the same way a car insurer looks at a safe driving record.
An insurer's underwriting process is basically a security audit in disguise. They actively reward businesses that can prove they have a mature, proactive handle on cyber risk. The stronger your defenses, the lower your premium.
Proving you're a low-risk client often comes down to showing you have specific, common-sense controls in place. Following established security frameworks, like the one from the National Institute of Standards and Technology (NIST), sends a clear message to underwriters. In fact, studies have shown that organizations following these types of guidelines have seen their annual premium increases be 3x lower than those that don't.
So, what specific actions will actually move the needle on your quote?
- Multi-Factor Authentication (MFA): For most insurers today, this is a deal-breaker. Implementing MFA on all critical systems—especially email and remote access—is one of the most powerful ways to shut down attackers.
- Employee Security Training: Human error is a factor in over 80% of breaches. Showing that you conduct regular training on phishing and other scams proves you're strengthening your weakest link: your people.
- Incident Response Plan (IRP): A documented IRP shows you’re prepared. It tells an insurer that you know exactly what to do when an attack hits, allowing you to contain the damage—and the cost of the claim—much faster.
- Data Backup and Recovery: Your best defense against ransomware is having reliable, tested, and isolated backups. Underwriters need to see that you can restore your operations without ever having to think about paying a ransom.
Investing in these areas does more than just protect your business—it builds a powerful case for a lower insurance premium. For a closer look at how all these elements affect your bottom line, our guide on cyber liability insurance cost breaks it down even further.
A Step-by-Step Guide to Getting Your Business Insured
Navigating the world of cyber liability insurance can feel overwhelming at first, but it's really a logical process. Think of it less like a final exam and more like an open conversation about your business's digital risks and the safeguards you already have.
Breaking it down into a few key steps will help you find the right policy with confidence, ensuring you're not just buying a piece of paper, but genuine protection.
Step 1: Assess Your Unique Cyber Risks
Before you even start looking at policies, you have to look in the mirror. You can't insure what you don't understand, so the first step is always a candid risk assessment. Where does your most sensitive data live? Who can access it? And what would the real-world fallout of a breach look like for your business?
Try to think in terms of specific, "what if" scenarios. For instance, what’s the plan if your entire customer database gets stolen and leaked? How long can you stay afloat if ransomware locks down your critical systems? Answering these tough questions is what helps you figure out exactly how much and what type of coverage you truly need.
Step 2: Gather Your Security Documentation
Insurance carriers will want to see what you're doing to protect yourself before they offer to cover you. The application is essentially a deep dive into your security posture, so getting your documentation ready ahead of time will make the whole process smoother.
Be prepared to provide details on things like:
- Data Backup Procedures: How often are you backing up essential data? Crucially, is it stored offline or on a separate, isolated network?
- Security Controls: Can you prove you're using the essentials like multi-factor authentication (MFA), up-to-date antivirus software, and a solid firewall?
- Employee Training Programs: Do you have a record of training your team to spot phishing emails and other common cyber threats?
A key piece of this puzzle is having a formal plan for when things go wrong. As you get ready to apply, you should build a comprehensive cybersecurity incident response plan. Insurers love to see this; it shows them you're a lower-risk client who is prepared to act quickly and effectively, which can often lead to better terms.
Step 3: Find a Specialized Insurance Broker
Let's be clear: not all insurance brokers are the same. Cyber risk is a complex and highly specialized field, and you absolutely want an expert in your corner—someone who deals with this day in and day out.
A good cyber insurance broker acts as your translator and advocate. They’ll help you connect your business risks to specific insurance needs, find carriers who actually understand your industry, and guide you through the often-tricky application process.
Pro Tip: Ask potential brokers about their experience with businesses just like yours—same size, same industry. A true specialist will already know the common threats you face and the fine print in a policy that will matter most to you.
Step 4: Complete the Application Honestly
The application is the bedrock of your insurance policy. This is not the place to fudge the details. Be completely transparent and accurate with every answer.
It might be tempting to downplay a past incident or overstate your security controls, but this is a surefire way to get a future claim denied. An inaccurate application can render your policy completely useless right when you need it most.
Step 5: Review Your Quote and Policy Details
Getting a quote is a milestone, not the finish line. Now it’s time to dig into the details with your broker. Scrutinize the fine print, paying close attention to the coverage limits, any sub-limits (which are smaller limits for specific types of claims), and the deductibles.
Make sure the policy aligns with the risks you identified back in step one. Does it have the right mix of first-party and third-party coverage for your specific needs? This final review is your last chance to make sure there are no unpleasant surprises waiting for you down the road.
Common Questions About Cyber Liability Insurance Answered
Even when you understand the concept of cyber liability insurance, it's the "what if" scenarios that really matter. Business owners need to know how a policy actually performs when a real crisis hits. Let's walk through some of the most common questions to clear up the confusion.
How Quickly Will the Policy Actually Help?
One of the biggest myths is that cyber insurance is just a check that arrives long after the disaster is over. The reality is, its most powerful benefits kick in almost immediately.
The moment you report a potential claim, your insurer will typically connect you with a pre-vetted incident response team. Think of them as the special forces of cyber crisis management. This team isn't just a single person; it's a coordinated group of legal counselors, IT forensic investigators, and public relations experts ready to jump in.
They get to work right away—often within hours—to:
- Figure out how the breach happened and plug the hole to stop more data from leaking.
- Carefully preserve evidence in a way that will hold up if you end up in court.
- Guide you through the maze of state and federal laws about notifying customers.
This rapid, hands-on support is often worth more than the financial payout itself. It's about containing the chaos before it can destroy your business. The financial reimbursement for lost income, legal fees, and other costs comes later, but the expert help starts on day one.
What Happens If My Security Isn't Perfect?
This is a huge source of anxiety for business owners. You might be thinking, "What if they find something wrong and deny my claim?" While insurers definitely expect you to have reasonable security measures in place, they don't expect your business to be an impenetrable fortress.
The key is showing you're actively managing your risk, not that you've achieved flawless security.
During the application process, the underwriter will take a look at your security setup. If they spot some weaknesses, it doesn't automatically mean you'll be denied. More often, they'll offer you a policy with a condition: you'll need to make specific upgrades, like adding multi-factor authentication, within a certain period. Of course, total neglect could lead to a denial, but showing you're willing to improve your defenses makes a big difference.
The underwriting process isn't about trying to catch you. It's about forming a partnership. The insurer needs to know you're doing your part, and they'll often work with you to get your security where it needs to be.
Does the Policy Cover Ransomware Payments?
Yes, in most cases. Modern cyber policies typically include coverage for cyber extortion, which is the category ransomware falls into. But it's not as simple as paying the ransom and forwarding the receipt to your insurance company.
When a ransomware attack happens, you don't go it alone. The insurer's incident response team steps in immediately. Their first goal is to try and restore your systems from backups so you don't have to pay anything. If restoring isn't an option, these specialists will often take over, negotiating directly with the criminals and verifying that paying the ransom is the only realistic way forward.
This expert-led approach keeps you from making a panicked decision and ensures that if a payment has to be made, it's handled as safely and effectively as possible.
Trying to figure out your cyber risk on your own can be overwhelming. At Wexford Insurance Solutions, we specialize in cutting through the noise to find the right cyber liability coverage for your specific business. Let us be your trusted partner in protecting what you've built. Speak with one of our specialists today to get started.
 What Is Umbrella Insurance and Why You Need It
What Is Umbrella Insurance and Why You Need It Professional Liability Insurance Coverage Explained
Professional Liability Insurance Coverage Explained